Don’t you just hate it when you buy a Pendrive or a Memory card and there’s nothing you can do to it? Whether it comes with software on it, or you’re just trying to use it for any other purpose, you should have the right to change things up however you like.
In this guide, you will be shown how to Remove Remove write protection in Pendrive and Memory Card. It’s a fairly simple process, so be sure to follow each and every step carefully. This guide is for information purposes and we are not responsible for anything that may happen to your device in the process.
Before we proceed, what is Write protection exactly? Write Protection is when the manufacturer locks the device down from being written on and prevents unauthorized access to add, change or delete the files on the device. While the uses of write protection are a good thing because it prevents files from being tampered with and the manufacturer can make sure all users are getting the same files, but it’s also very inconvenient. To remove this protection, you will need to format the drive.
In this guide, I will show you exactly how to do that. Follow each and every step carefully, please. Windows platform is used for the purpose of this guide.

HOW TO REMOVE REMOVE WRITE PROTECTION IN PENDRIVE?
Step 1: Plugin your pen drive into your USB 2.0 on your computer. To make sure the computer has read your pen drive, you can go down to your bottom left on Windows, you will notice a small USB drive icon. If you click that, it will say “Removable Disk.” This means that the pen drive has been read successfully. You can take a backup of your files from the pen drive or Memory card Because we here are going to format it Completely.
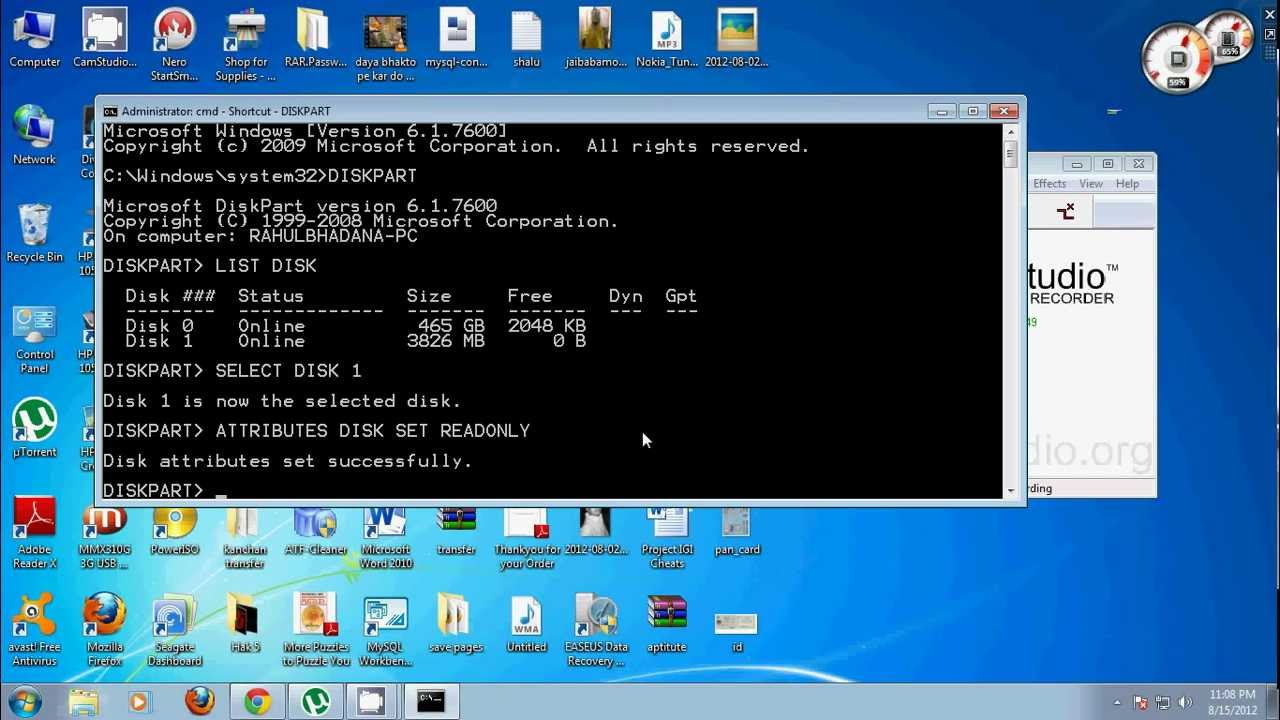
Step 2: Next we need to open up the command prompt. You can do this by simply going to “Start”, then just search for “Command Prompt”, or you can simply just type in “cmd” and a command prompt should pop up.
Step 3: In the command prompt, type in the drive letter of your pen drive with a colon at the end, like this: “ F: ” but without the quotation marks.
Step 4: After putting in the previous command, type in “format” without the quotation marks. Here’s how to do it: “format F:” and then press “Enter.”
This should get the process started to Remove write protection in Pendrive. Make sure that you are entering the right command with the right drive letter. If you have more than one pen drive plugged in, make sure that you do select the right one as you can accidentally format the wrong drive, causing loss of data.
Step 5: After the process is complete, proceed to the close command prompt.