There may be more fun things coming in your mind already, How about “via Potato ” or “via GTA 5″ or ” via Calculator” why not, it can be anything that you can best think of. So let's move on and see how to Post Custom Via Status on Facebook. Continue reading the below Simple steps, and you will learn it easily.
STEPS TO POST CUSTOM VIA STATUS ON FACEBOOK
Step 1: First of all To Post Custom Via Status on Facebook, you will need to create an app on Facebook, Nope that's not hard at all, you don't need to do any Coding, Follow me while I show you how to do it.
Step 2: Click here to go to the Facebook Developer page, there if you are asked to register as a developer, read this step and if you are not asked and you are already registered then skip to Step 3.
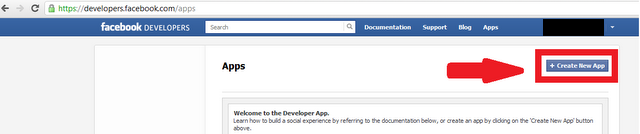
Click on Register as a developer and Check the box ” I accept the Facebook Platform Policy and the Facebook Privacy Policy” and Click on Continue > Continue > Done.
Step 3: Now you are Registered as Developer, Now click on Create a new app, Next Step is to name your App so Name it anything that you want to show as “updated via XYZ”. Here in my case it will show ” updated via Smarttricks.net ” as I have named it Smarttricks.net as you can see in the below picture. Now click on Continue, Leave everything else as it is.

Step 4: On the next page you will be filling some more details like App domain and Site URL, As you can see I have entered my site URL in both the Cases. Everything is done now Click on Save Changes. Note the APP ID we will need it in Next Step

Step 5: You app is Ready, Now its time to use it. Simply Copy the Below URL, Open a new tab in your Browser, Paste it in the address bar, You will have to Replace my APP ID with yours in following URL which is Highlighted in Green Color,
Also Understand that if you want to Redirect your Friends to your own blog when they try and click on your Custom Via Status, then Replace www.smarttricks.net with yours in the above URL.
Step 6: Once you have Replaced the app id and Pasted the URL in your address bar, hit enter and boom, you will see something like below Pic, obviously with your app name.
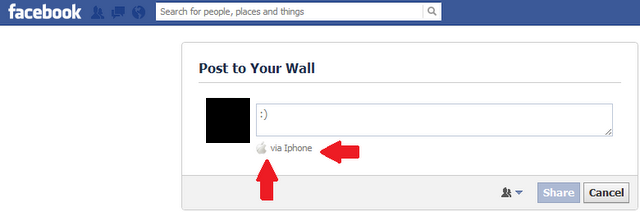
Step 7: Now its time to let your friends know about this, Write your status and click on Share. You will be redirected to Smarttricks.net but its time to check your timeline to see your Custom via Facebook Status.
Conclusion :
So Now in this article, you learned how to create your own App and how to Post Custom Via Status on Facebook. If In Case you find it Tedious, then I will share one more method, you simply go and click on any name you want as updated via of your choice and you will be taken to the status update page directly.
So Now in this article, you learned how to create your own App and how to Post Custom Via Status on Facebook. If In Case you find it Tedious, then I will share one more method, you simply go and click on any name you want as updated via of your choice and you will be taken to the status update page directly.
You might be thinking why so long process when you can do it with this site way to easy? Well, My main aim was to explain the whole process of how it works. and on the above-mentioned site, you are limited to choose the name from the option provided. it's always better to make your own choice of a custom name.